Duo integrates with your Cisco ASA VPN to add two-factor authentication to any VPN login. Overview This Duo SSL VPN configuration supports and the for web-based VPN logins, and push, phone call, or passcode authentication for desktop and mobile client connections that use SSL encryption. The do not feature the interactive Duo Prompt for web-based logins, but does capture client IP informations for use with, such as geolocation and authorized networks. The feature inline enrollment and the interactive Duo Prompt for both web-based VPN logins and AnyConnect 4.6+ client logins. This deployment option requires that you have a SAML 2.0 identity provider in place that features Duo authentication, like the.
Primary and Duo secondary authentication occur at the identity provider, not at the ASA itself. Please refer to the to learn more about the different options for protecting ASA logins with Duo MFA. If you need to protect connections that use Cisco's desktop VPN client (IKE encryption), use our. Before starting, make sure that Duo is compatible with your Cisco ASA device. Log on to your Cisco ASDM interface and verify that your Cisco ASA firmware is version 8.3 or later. First Steps You should already have a working primary authentication configuration for your SSL VPN users before you begin to deploy Duo, e.g.
Windows Registry Editor Version 5.00. Questions & Answers related to Cisco AnyConnect VPN Client. Cisco Silent Installation By. May 19, 2016 - Use this option only if you cannot install the Cisco AnyConnect VPN Client on your laptop. To NSO WinSCP For file transfers to/from NSO Text Editors Notepad++. Documentation NETSIM Network Simulator • Run the installation $ sh. Packages • Creates a default ncs.conf $ source ~/ncs/3.3/ncsrc.
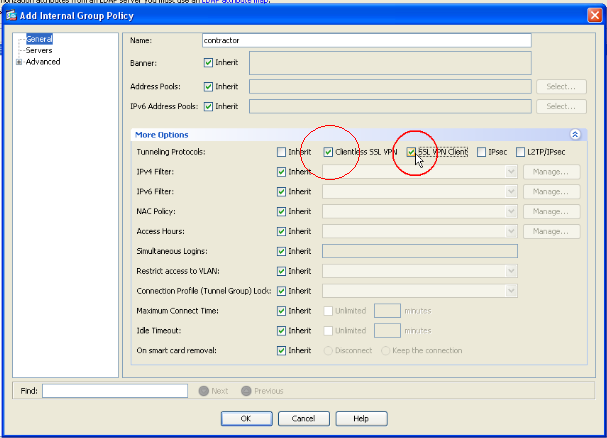
LDAP authentication to Active Directory. Then you'll need to: •.
• Log in to the and navigate to Applications. Edirol super quartet vst. • Click Protect an Application and locate Cisco SSL VPN in the applications list. Click Protect this Application to get your integration key, secret key, and API hostname.
(See for help.) • Download the Duo Cisco package from your Cisco SSL VPN application's properties page in the Duo Admin Panel, and unzip it somewhere convenient such as your desktop. Treat your secret key like a password The security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Modify the sign-in page To add the Duo customization to your Cisco sign-in page: • Log on to your Cisco ASA administrator web interface (ASDM). • Click the Configuration tab and then click Remote Access VPN in the left menu. • Navigate to Clientless SSL VPN Access → Portal → Web Contents. Then click Import. • In the Source section, select Local computer, click Browse Local Files., and find the Duo-Cisco-vX.js file extracted from the Duo-Cisco-v X- accountid.zip file downloaded earlier from the Duo admin console where v X will reflect the actual version of the Duo Cisco package and accountid is your organization's Duo Account ID (visible on the Settings tab of the Duo Admin Panel) i.e. Duo-Cisco- v5- 1234-5678-90.zip).
After the file is selected, Duo-Cisco-v X.js will appear in the Web Content Path box. • In the Destination section, select No in response to 'Require authentication to access its content?' • Click Import Now then click Apply • Navigate to Clientless SSL VPN Access → Portal → Customization, select the Customization Object you want to modify, and then click Edit.
• In the outline on the left, click Title Panel (under Logon Page). • Then type (replacing v X with the file version actually downloaded) in the Text: box. • Click Apply Add the Duo LDAP server • Navigate to AAA/Local Users → AAA Server Groups, click Add, and fill out the form: Server Group Duo-LDAP Protocol LDAP • Click OK. • Select the Duo-LDAP group you just added.